The Quantum Technology Ecosystem – Explained
Steve Blank
MARCH 22, 2022
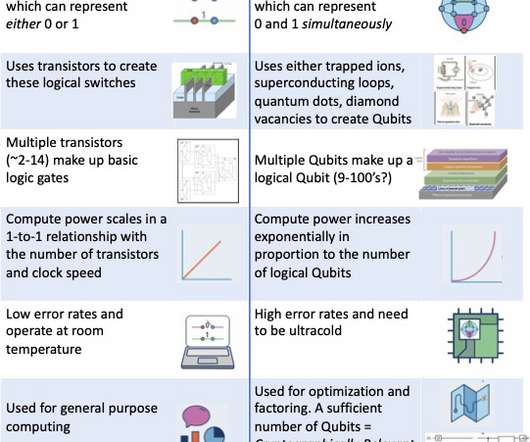
Not only would a Universal Quantum Computer running Shor’s algorithm make today’s public key algorithms (used for asymmetric key exchanges and digital signatures) useless, someone can implement a “harvest-now-and-decrypt-later” attack to record encrypted documents now with intent to decrypt them in the future. Quantum Timing.








Let's personalize your content