You Don’t Need Permission
Steve Blank
JUNE 4, 2021
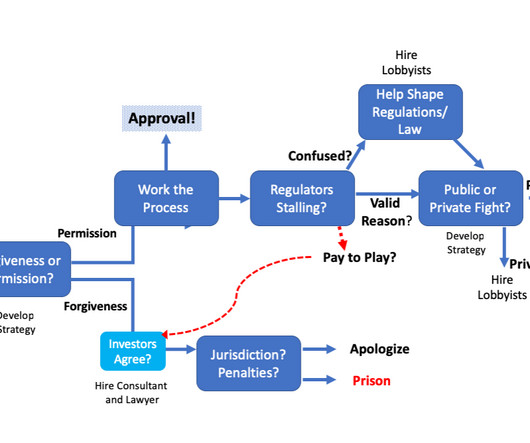
As head of sales and marketing, Suresh didn’t need his CEO to buy into the process or give his permission to start the discovery process. If you’re in charge or part of a customer-facing organization, you don’t need to wait for permission to talk to customers to test hypotheses. He was in charge. Lessons Learned.
















































Let's personalize your content