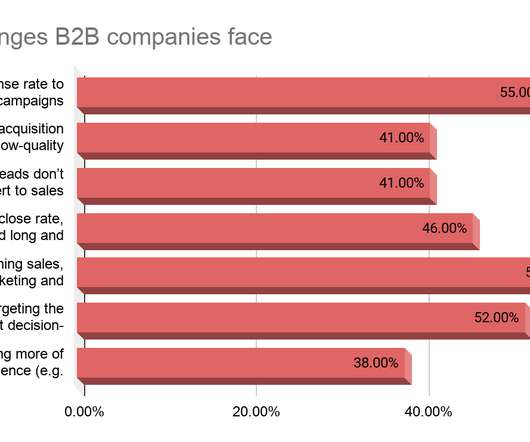
Common B2B Challenges and How To Solve Them
ConversionXL
MARCH 17, 2021
In 2020 we applied the same approach to two of our customers: idronect (software to manage drone businesses) and Opsfleet (software development company). With Opsfleet, the situation was critical as they provide a commodity service (software development) and have signifcant competition.



















Let's personalize your content